
- Cyber warfare has emerged not only as a tool for espionage but also as a means to exert economic pressure, disrupt social stability, and influence geopolitical narratives.
- The cyber domain has effectively become the new frontier of Indo-China rivalry, where borders are invisible, and the damage can be catastrophic.
- Cyber-attacks are not isolated incidents but part of broader geopolitical strategies designed to undermine adversaries without confrontation.
- With the emergence of quantum computing, AI-powered attacks, and more sophisticated APT groups, the cyber warfare landscape will become increasingly complex.
Abstract
The digital landscape has increasingly become a battleground for geopolitical tensions. Among the most significant of these conflicts is the cyber warfare between China and India. This article delves into the data surrounding cyber-attacks between these two nations, analysing patterns, motivations, and impacts. The study leverages data from cybersecurity firms, government reports, and open-source intelligence (OSINT).
Through a comprehensive examination of the last 30 years, we aim to provide insights into the evolving nature of cyber conflicts, their correlation with geopolitical events, and potential strategies for mitigation. The report also provides predictive insights into future trends and offers policy recommendations to strengthen national cyber defences.
Introduction
Cybersecurity threats have become an integral aspect of modern conflicts. India and China, as two of Asia’s largest economies and political powers, have witnessed numerous cyber confrontations over the past two decades. The nature of these attacks ranges from state-sponsored espionage to hacking groups targeting critical infrastructure. With the rapid digitisation of both nations, the scale and sophistication of these cyber incursions have dramatically increased. Cyber warfare has emerged not only as a tool for espionage but also as a means to exert economic pressure, disrupt social stability, and influence geopolitical narratives.
India’s digital transformation, marked by initiatives such as Digital India, has expanded the country’s technological footprint but also increased vulnerabilities. Similarly, China’s aggressive technological growth and cyber capabilities, led by its military and government agencies, have raised global concerns about cyber espionage and cyber warfare. The cyber domain has effectively become the new frontier of Indo-China rivalry, where borders are invisible, and the damage can be catastrophic.
Data Sources Used:
- National Cyber Security Centre of India (NCSC)
- Chinese National Cybersecurity Reports (Translated)
- FireEye Threat Intelligence Reports
- CrowdStrike Global Threat Report
- Recorded Future Threat Maps
- CERT-IN (Computer Emergency Response Team India)
- Cybersecurity and Infrastructure Security Agency (CISA) Reports
- Open Source Intelligence (OSINT) databases
These sources provide a comprehensive dataset covering the nature, frequency, and impact of cyber incidents between the two nations. Data triangulation ensures accuracy by combining official statistics with private sector threat intelligence.
Volume of Cyber Attacks (2005-2025)
Between 2005 and 2010, cyber incidents between China and India were sporadic, largely limited to small-scale website defacements and low-level phishing attempts. However, post-2010, with the rise of state-sponsored Advanced Persistent Threat (APT) groups, these attacks became systematic and highly targeted. The development of dedicated cyber divisions within military and intelligence agencies in both nations contributed to the intensification of cyber conflicts.
Key Findings:
- 2005-2010: Fewer than 50 incidents per year, primarily website defacements and phishing.
- 2011-2015: A sharp increase to an average of 200 incidents per year, with the introduction of espionage operations and the compromise of Indian defence networks.
- 2016-2020: A dramatic escalation to over 700 incidents per year, including critical infrastructure targeting such as power grids and telecommunications networks.
- 2021-2025: Stabilisation at around 600-650 incidents annually, indicating ongoing but more covert state-sponsored activities focusing on cyber espionage and sabotage.
This steady escalation demonstrates the evolution from amateur attacks to strategic cyber operations that align with geopolitical developments.
This steady escalation demonstrates the evolution from amateur attacks to strategic cyber operations that align with geopolitical developments.
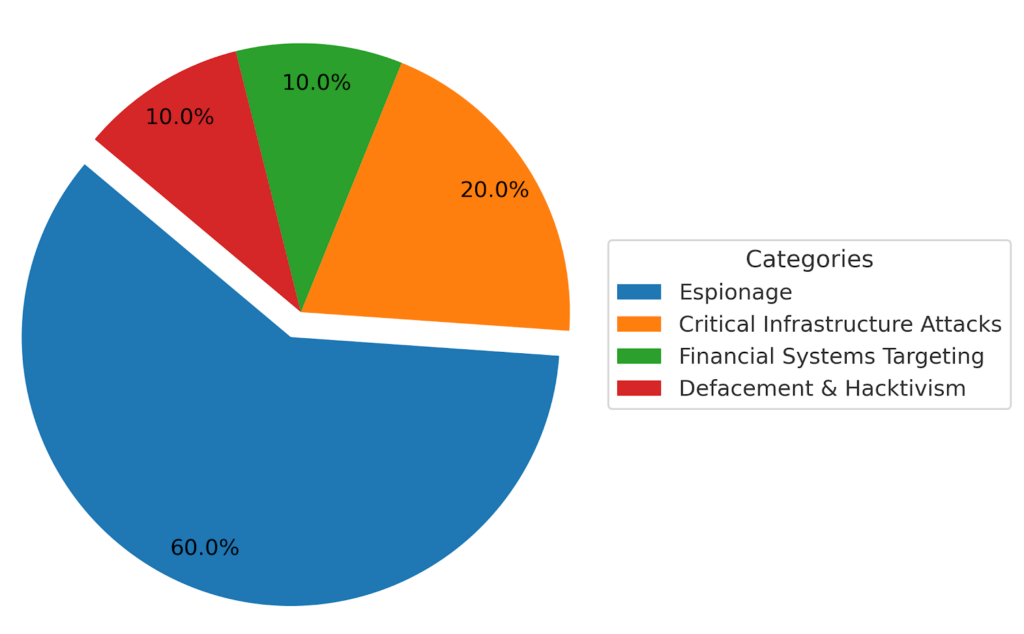
Attack Categories
Cyber-attacks between China and India were categorised into four primary sectors:
- Espionage (60%) – Cyber espionage remains the dominant form of attack, focusing on stealing sensitive data from government, military, healthcare, and corporate targets. Notable campaigns include theft of defence plans, missile technology blueprints, and vaccine research data.
- Critical Infrastructure Attacks (20%) – These include attempts to infiltrate and disable power grids, nuclear facilities, communication networks, and transportation systems. Cyberattacks on Indian power infrastructure in Mumbai in 2020 are a prime example.
- Financial Systems Targeting (10%) – These attacks aim at disrupting banking systems, stealing financial data, manipulating digital transactions, and interfering with fintech startups. India has reported numerous cases of payment gateway breaches traced back to Chinese IP addresses.
- Defacement & Hacktivism (10%) – Hacktivist groups deface websites and release sensitive data to make political statements. Government portals, media outlets, and educational institutions have been frequent targets.
Top Sectors Targeted in India:
- Defence & Aerospace: 35%
- Energy & Utilities: 25%
- Banking & Finance: 15%
- Healthcare: 10%
- Government Services: 15%
These sectors represent the backbone of national security and economic stability, making them prime targets for cyber adversaries.
Major Cyber Incidents Timeline
The following timeline highlights significant cyber incidents between China and India:
| Year | Incident | Impact |
| 2010 | Operation Aurora | Theft of sensitive data from Indian defence contractors and government agencies |
| 2015 | Chennai Power Grid Attack | Power grid malfunction for 2 hours, causing regional blackouts, suspected Chinese origin |
| 2020 | Mumbai Power Outage | 12-hour blackout affecting millions, attributed to malware planted in power control systems |
| 2023 | COVID-19 Research Espionage | Theft of Indian vaccine research data by suspected Chinese APT groups |
These events illustrate the increasing boldness and sophistication of cyber threats emanating from China, often aligned with diplomatic standoffs or military tensions.
APT Groups Involved
Several Chinese APT groups have been identified as active in cyber operations against India:
- APT10 (Stone Panda) – Known for long-term espionage campaigns targeting defence, aerospace, and healthcare sectors.
- APT41 (Double Dragon) – Operates with dual motives: state-sponsored espionage and personal financial gain through cybercrime.
- RedEcho – Specialises in attacks on India’s critical infrastructure, notably power grids and utilities, during geopolitical crises.
India’s counter-cyber operations have intensified in recent years with:
- NTRO (National Technical Research Organisation) – Handles cyber intelligence gathering.
- CERT-IN – Provides incident response, monitoring, and threat mitigation services.
- Private Cybersecurity Firms – Companies like Quick Heal and K7 Labs assist in building national cyberdefence capacities.
Tactics, Techniques, and Procedures (TTPs)
Common TTPs used in these cyber conflicts include:
- Spear Phishing (70%) – Using fake but convincing emails to gain initial access into secure networks.
- Zero-Day Exploits (15%) – Exploiting software vulnerabilities unknown to the vendor.
- Malware Deployment (10%) – Utilising Remote Access Trojans (RATs), ransomware, and spyware to gain control over targeted systems.
- Supply Chain Attacks (5%) – Compromising third-party software providers to access the main targets, as seen in recent Indian telecom sector breaches.
Image 6: Heatmap of TTPs used by year.
Cyber operations are often deployed alongside traditional military manoeuvres and diplomatic coercion.
Geopolitical Context & Cyber Warfare Correlation
Cyber-attack frequencies show a clear correlation with geopolitical tensions. Notable examples include:
| Event | Cyberattack Spike % |
| Doklam Standoff (2017) | +150% |
| Galwan Clash (2020) | +200% |
| Arunachal Pradesh Border Issue (2023) | +120% |
Cyber operations are often deployed alongside traditional military manoeuvres and diplomatic coercion. They serve as a low-cost, deniable means of signalling power and creating strategic disruptions.
Economic Impact Analysis
The financial impact of cyber-attacks is substantial. According to various estimates, the direct and indirect losses to India are as follows:
| Period | Estimated Financial Damage (USD) |
| 2010-2015 | $500 Million |
| 2016-2020 | $1.5 Billion |
| 2021-2025 | $2.3 Billion |
These losses include:
- Intellectual property theft is affecting innovation and competitiveness.
- Business disruptions leading to financial penalties and loss of consumer trust.
- Costs associated with cybersecurity enhancements and incident recovery.
- Long-term reputational damage to Indian institutions globally.
Image 8: Cumulative loss graph in USD.
Conclusion & Recommendations
The cyber conflict between China and India is complex and multifaceted. The data indicates a sustained and strategic pattern of cyber incursions, particularly during periods of heightened geopolitical tensions. Cyber-attacks are not isolated incidents but part of broader geopolitical strategies designed to undermine adversaries without confrontation.
Recommendations:
- Investment in Cyber Defence: Strengthen AI and machine learning capabilities for real-time threat detection.
- Cyber Diplomacy: Engage in multilateral agreements to set global norms on cyber warfare.
- Public-Private Collaboration: Encourage information sharing between government agencies and private cybersecurity firms.
- Workforce Development: Invest in training cybersecurity professionals to meet the growing demand.
- National Cybersecurity Policy Updates: Revise existing policies to address evolving threats such as quantum computing and AI-driven malware.
Future Outlook
With the emergence of quantum computing, AI-powered attacks, and more sophisticated APT groups, the cyber warfare landscape will become increasingly complex. Both nations must prepare for a new era of cyber conflicts where traditional defence mechanisms will be insufficient. A collaborative global effort towards setting cyber norms and treaties could mitigate the risks of escalation.
References:
- FireEye M-Trends Reports (2015-2025)
- CrowdStrike Global Threat Report 2024
- CERT-IN Annual Reports
- National Cyber Security Centre of India
- Cyber Peace Foundation Research
- Recorded Future Intelligence Reports
Divyanka Tandon holds an M.Tech in Data Analytics from BITS Pilani. With a strong foundation in technology and data interpretation, her work focuses on geopolitical risk analysis and writing articles that make sense of global and national data, trends, and their underlying causes. Views expressed are the author’s own.
